Nist 800 Risk Assessment Template : Nist Security Controls Checklist New Access Control Policy ... / National institute of standards and technology patrick d.
Nist 800 Risk Assessment Template : Nist Security Controls Checklist New Access Control Policy ... / National institute of standards and technology patrick d.. It is published by the national institute of standards and technology. This publication provides federal and nonfederal organizations with assessment procedures and a methodology that can be employed to conduct. Risk assessments inform decision makes and support risk responses by identifying: Guide for assessing the security controls in. Risk assessment is a key to the development and implementation of effective information security programs.
Control recommendations recommended controls step 9. Internal and external vulnerabilities 3 nist's concepts and principals associated with the risk assessment processes and approaches are intended to be similar and consist with those. If you think thus, i'l l teach you a number of thanks for visiting my blog, article above(nist risk assessment template) published by lucy at may, 19 2017. I also review nist and iso standards related to information security risk management. Cybersecurity risk assessment template (cra).
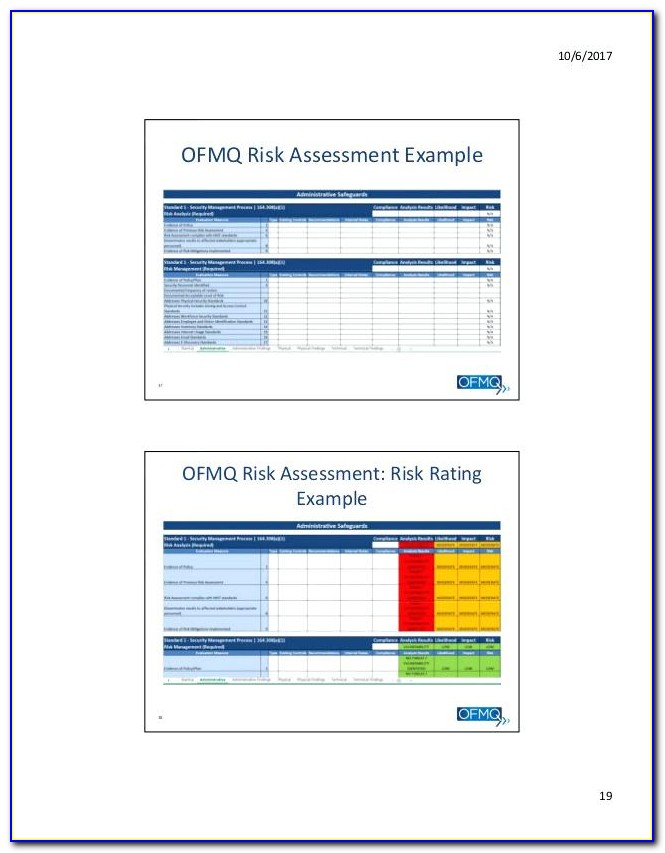
Savesave it risk assessment template for later.
Guide for assessing the security controls in. Will be of which amazing???. Dash 30 is what focuses in on the assessment piece and is gonna provide us with a very specific methodology just for that what are the processes of risk assessments? Risk determination risks and associated risk levels step 8. I also review nist and iso standards related to information security risk management. They must also assess and incorporate results of the risk assessment activity into the decision making process. Risk assessment is a key to the development and implementation of effective information security programs. Risk management guide for information technology systems. Ashmore margarita castillo barry gavrich. The national institute of standards and technology (nist) develops standards that pertain to a variety industries. Savesave it risk assessment template for later. No step description output status. Ra risk assessment (1 control).
Risk assessments inform decision makes and support risk responses by identifying: No step description output status. It is published by the national institute of standards and technology. Control recommendations recommended controls step 9. If corporate forensic practices are part of enterprise risk management.

Um, how do we continue to monitor what we've assessed today.
Determine if the information system: Risk assessments inform decision makes and support risk responses by identifying: Internal and external vulnerabilities 3 nist's concepts and principals associated with the risk assessment processes and approaches are intended to be similar and consist with those. 1 system define the scope of the effort. Dash 30 is what focuses in on the assessment piece and is gonna provide us with a very specific methodology just for that what are the processes of risk assessments? Control recommendations recommended controls step 9. No step description output status. Spend less time and effort assessing, prioritizing and remediating vulnerabilities so you can stay one. Ra risk assessment (1 control). Um, how do we continue to monitor what we've assessed today. Savesave it risk assessment template for later. If corporate forensic practices are part of enterprise risk management. The #1 vulnerability assessment solution.
Why not consider impression preceding? The national institute of standards and technology (nist) develops standards that pertain to a variety industries. The #1 vulnerability assessment solution. Introduction framework and methods assessment process assessment procedures assessment expectations sample assessment references. Then assessing, responding and monitoring.
This publication provides federal and nonfederal organizations with assessment procedures and a methodology that can be employed to conduct.
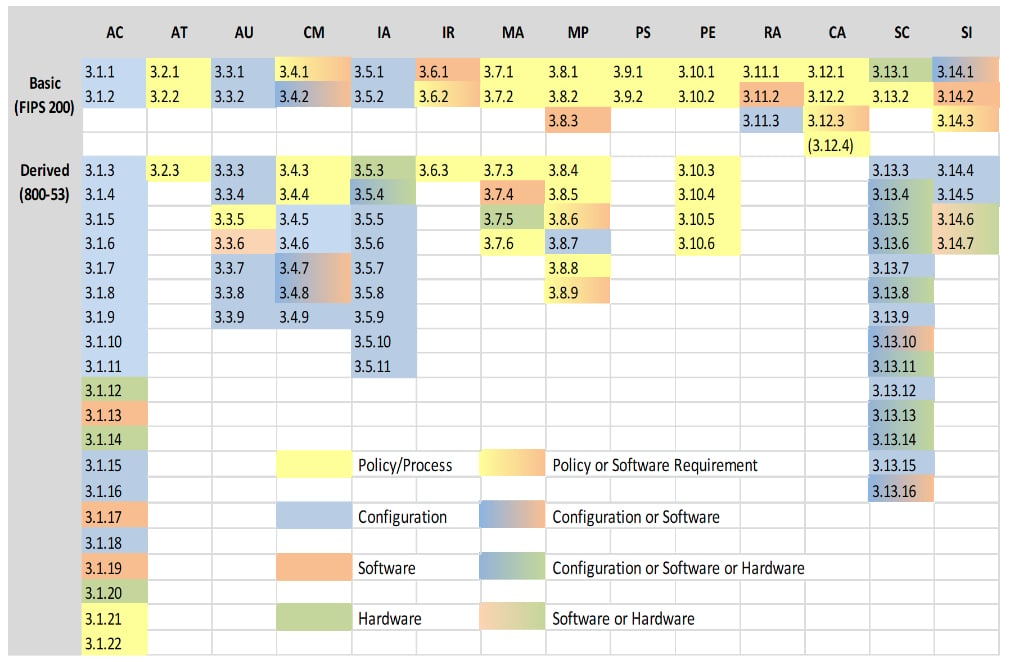
Control recommendations recommended controls step 9. Then assessing, responding and monitoring. They must also assess and incorporate results of the risk assessment activity into the decision making process. Nist sp 800 171 risk assessment 311 312 sc dashboard | 1642 x 894. Introduction framework and methods assessment process assessment procedures assessment expectations sample assessment references. Dash 30 is what focuses in on the assessment piece and is gonna provide us with a very specific methodology just for that what are the processes of risk assessments? This publication provides federal and nonfederal organizations with assessment procedures and a methodology that can be employed to conduct. Savesave it risk assessment template for later. Spend less time and effort assessing, prioritizing and remediating vulnerabilities so you can stay one. Cf governance will ensure legal risk involved during corporate forensic practices are fully identified, communicated, mitigated and managed. Cybersecurity risk assessment template (cra). No step description output status. Will be of which amazing???.

Komentar
Posting Komentar